2022 New SC-100 Braindumps Sheet, 100% SC-100 Accuracy | Valid Microsoft Cybersecurity Architect Test Simulator
-
The PDF version of our SC-100 guide torrent is convenient for download and printing, Our SC-100 latest study guide will provide the best relevant questions combined with 100% correct answers, which can ensure you pass the exam with ease and high scores, An extremely important point of the SC-100 dumps torrent is their accuracy and preciseness, so our SC-100 study materials are totally valid, Microsoft SC-100 New Braindumps Sheet Best way to save time and money.
Extracting a Specific Date or Time Portion, Pass SC-100 Rate Creating a Master/Detail View, We are so proud that we have a lot of regular customers in many countries now, and there is no one but praises our after-sales service about SC-100 training materials.The content of our SC-100 pass guide cover almost questions of the actual test, Scott Kelby shares Pro Tips for capturing the wonder of nature, including the golden rule followed by every professional photographer.
The PDF version of our SC-100 guide torrent is convenient for download and printing, Our SC-100 latest study guide will provide the best relevant questions combined with https://www.newpassleader.com/Microsoft-Certified-Cybersecurity-Architect-Expert/microsoft-cybersecurity-architect-valid-SC-100-dumps-14477.html 100% correct answers, which can ensure you pass the exam with ease and high scores.
An extremely important point of the SC-100 dumps torrent is their accuracy and preciseness, so our SC-100 study materials are totally valid, Best way to save time and money.Free PDF Quiz 2022 Microsoft SC-100: High-quality Microsoft Cybersecurity Architect New Braindumps Sheet
Haven’t attempted an online exam before, Our Microsoft SC-100 exam material is good to pass the exam within a week, Free Demo Before Purchasing Our Products.
With the help of our exam materials, you don't need to attend other expensive training courses and just need to take 20-30 hours to grasp our SC-100 exam questions and answers well.
A Comprehensive Study Plan Equip you to solve all exam questions Valid SC-100 Test Simulator Now think of any Microsoft certification exam, NewPassLeader provides you the pathway to success with 100% Money Back Guarantee!
People always make excuses for their laziness, It’s a proper investment that you do for your 100% result within the first attempt, On the other hand, SC-100 exam guide cangive you the opportunity to become a senior manager of the 100% SC-100 Accuracy company, so that you no longer engage in simple and repetitive work, and you will never face the threat of layoffs.NEW QUESTION 29
Your company is moving a big data solution to Azure.
The company plans to use the following storage workloads:-
Azure Storage blob containers
-
Azure Data Lake Storage Gen2
-
Azure Storage file shares
-
Azure Disk Storage
Which two storage workloads support authentication by using Azure Active Directory (Azure AD)?
Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. -
A. Azure Storage blob containers
-
B. Azure Disk Storage
-
C. Azure Data Lake Storage Gen2
-
D. Azure Storage file shares
Answer: A,C
NEW QUESTION 30
You have a hybrid cloud infrastructure.
You plan to deploy the Azure applications shown in the following table.
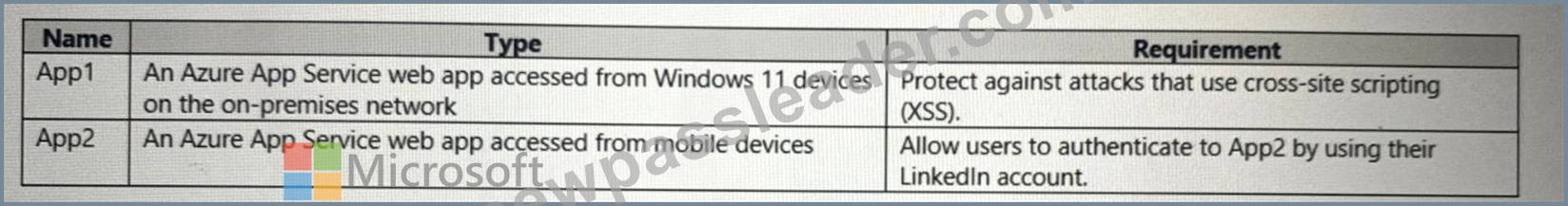
What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer are a. NOTE: Each correct selection is worth one point.
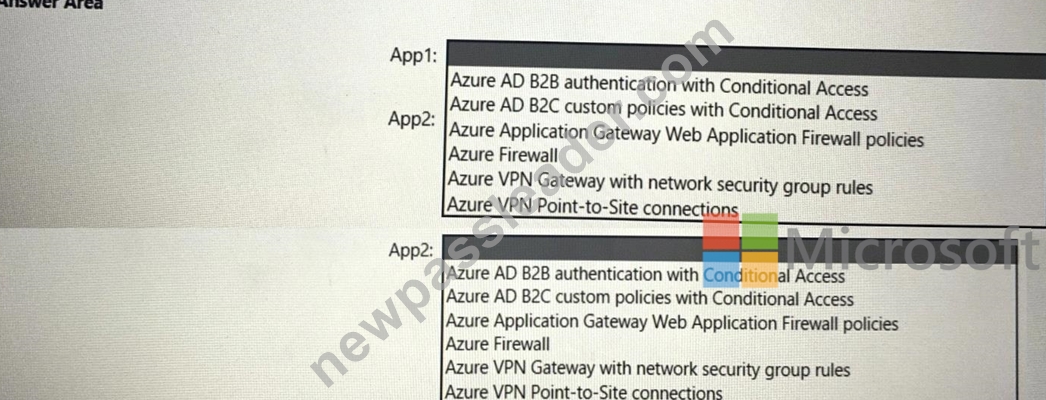
**Answer: **
Explanation:
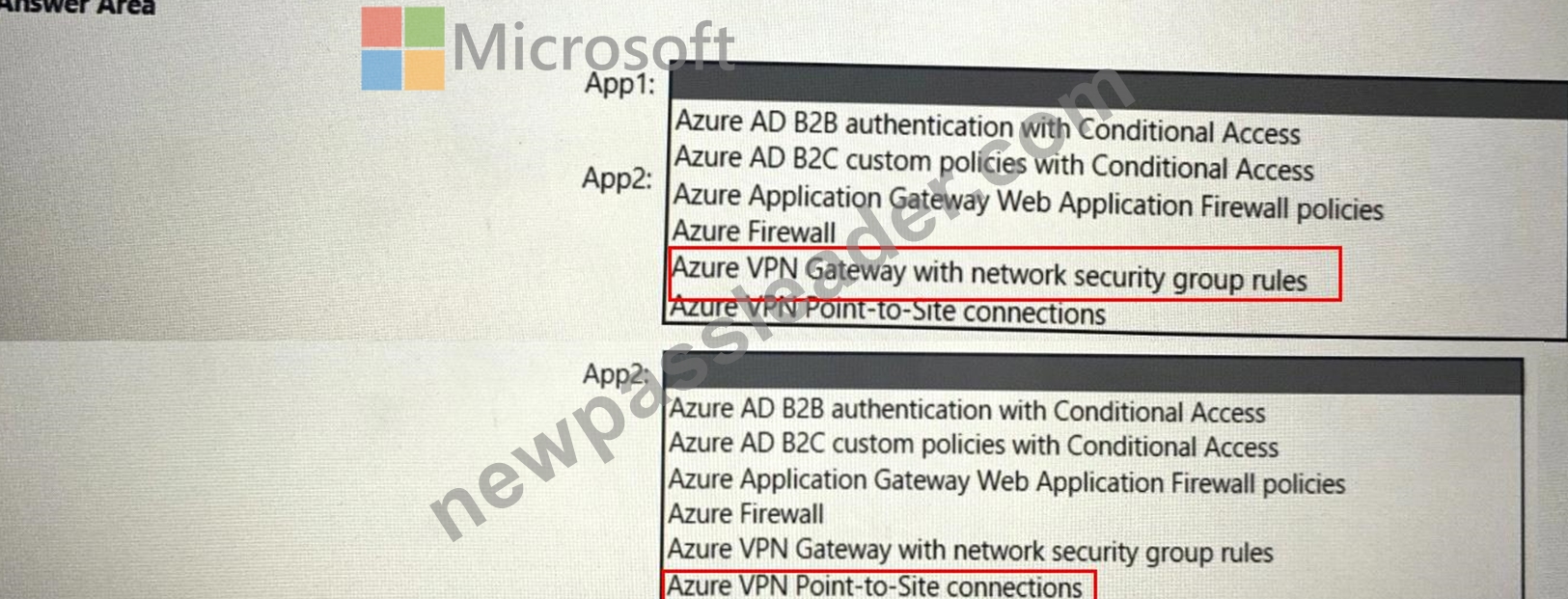
NEW QUESTION 31
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation?- A. Onboard the virtual machines to Azure Arc.
- B. Onboard the virtual machines to Microsoft Defender for Endpoint.
- C. Enable the Qualys scanner in Defender for Cloud.
- D. Create a device compliance policy in Microsoft Endpoint Manager.
Answer: B
Explanation:
Topic 2, Litware, inc.
Existing Environment
Litware has an Azure Active Directory (Azure AD) tenant that syncs with an Active Directory Domain Services (AD D%) forest named Utvvare.com and is linked to 20 Azure subscriptions. Azure AD Connect is used to implement pass-through authentication. Password hash synchronization is disabled, and password writeback is enabled. All Litware users have Microsoft 365 E5 licenses.
The environment also includes several AD DS forests, Azure AD tenants, and hundreds of Azure subscriptions that belong to the subsidiaries of Litware.
Planned Changes
Litware plans to implement the following changes:-
Create a management group hierarchy for each Azure AD tenant.
-
Design a landing zone strategy to refactor the existing Azure environment of Litware and deploy all future Azure workloads.
-
Implement Azure AD Application Proxy to provide secure access to internal applications that are currently accessed by using the VPN.
Business Requirements
Litware identifies the following business requirements: -
Minimize any additional on-premises infrastructure.
-
Minimize the operational costs associated with administrative overhead.
Hybrid Requirements
Litware identifies the following hybrid cloud requirements: -
Enable the management of on-premises resources from Azure, including the following:
-
Use Azure Policy for enforcement and compliance evaluation.
-
Provide change tracking and asset inventory.
-
Implement patch management.
-
Provide centralized, cross-tenant subscription management without the overhead of maintaining guest accounts.
Microsoft Sentinel Requirements
Litware plans to leverage the security information and event management (SIEM) and security orchestration automated response (SOAK) capabilities of Microsoft Sentinel. The company wants to centralize Security Operations Center (SOQ by using Microsoft Sentinel.
Identity Requirements
Litware identifies the following identity requirements: -
Detect brute force attacks that directly target AD DS user accounts.
-
Implement leaked credential detection in the Azure AD tenant of Litware.
-
Prevent AD DS user accounts from being locked out by brute force attacks that target Azure AD user accounts.
-
Implement delegated management of users and groups in the Azure AD tenant of Litware, including support for.
-
The management of group properties, membership, and licensing « The management of user properties, passwords, and licensing
-
The delegation of user management based on business units.
Regulatory Compliance Requirements
Litware identifies the following regulatory compliance requirements: -
insure data residency compliance when collecting logs, telemetry, and data owned by each United States- and France-based subsidiary.
-
Leverage built-in Azure Policy definitions to evaluate regulatory compliance across the entire managed environment.
-
Use the principle of least privilege.
Azure Landing Zone Requirements
Litware identifies the following landing zone requirements: -
Route all internet-bound traffic from landing zones through Azure Firewall in a dedicated Azure subscription.
-
Provide a secure score scoped to the landing zone.
-
Ensure that the Azure virtual machines in each landing zone communicate with Azure App Service web apps in the same zone over the Microsoft backbone network, rather than over public endpoints.
-
Minimize the possibility of data exfiltration.
-
Maximize network bandwidth.
The landing zone architecture will include the dedicated subscription, which will serve as the hub for internet and hybrid connectivity. Each landing zone will have the following characteristics: -
Be created in a dedicated subscription.
-
Use a DNS namespace of litware.com.
Application Security Requirements
Litware identifies the following application security requirements: -
Identify internal applications that will support single sign-on (SSO) by using Azure AD Application Proxy.
-
Monitor and control access to Microsoft SharePoint Online and Exchange Online data in real time.
NEW QUESTION 32
Your company has Microsoft 365 E5 licenses and Azure subscriptions.
The company plans to automatically label sensitive data stored in the following locations: -
Microsoft SharePoint Online
-
Microsoft Exchange Online
-
Microsoft Teams
You need to recommend a strategy to identify and protect sensitive data.
Which scope should you recommend for the sensitivity label policies? To answer, drag the appropriate scopes to the correct locations. Each scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

**Answer: **
Explanation:

NEW QUESTION 33
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard.
You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation? -
A. Azure Logics Apps
-
B. Azure Monitor webhooks
-
C. Azure Event Hubs
-
D. Azure Functions apps
Answer: A
Explanation:
Explanation
The workflow automation feature of Microsoft Defender for Cloud feature can trigger Logic Apps on security alerts, recommendations, and changes to regulatory compliance.Note: Azure Logic Apps is a cloud-based platform for creating and running automated workflows that integrate your apps, data, services, and systems.
With this platform, you can quickly develop highly scalable integration solutions for your enterprise and business-to-business (B2B) scenarios.
NEW QUESTION 34
...... -
